| Parameter | Description |
|---|---|
| /agree | Implicitly agrees to the license agreement window pop-up without showing it. |
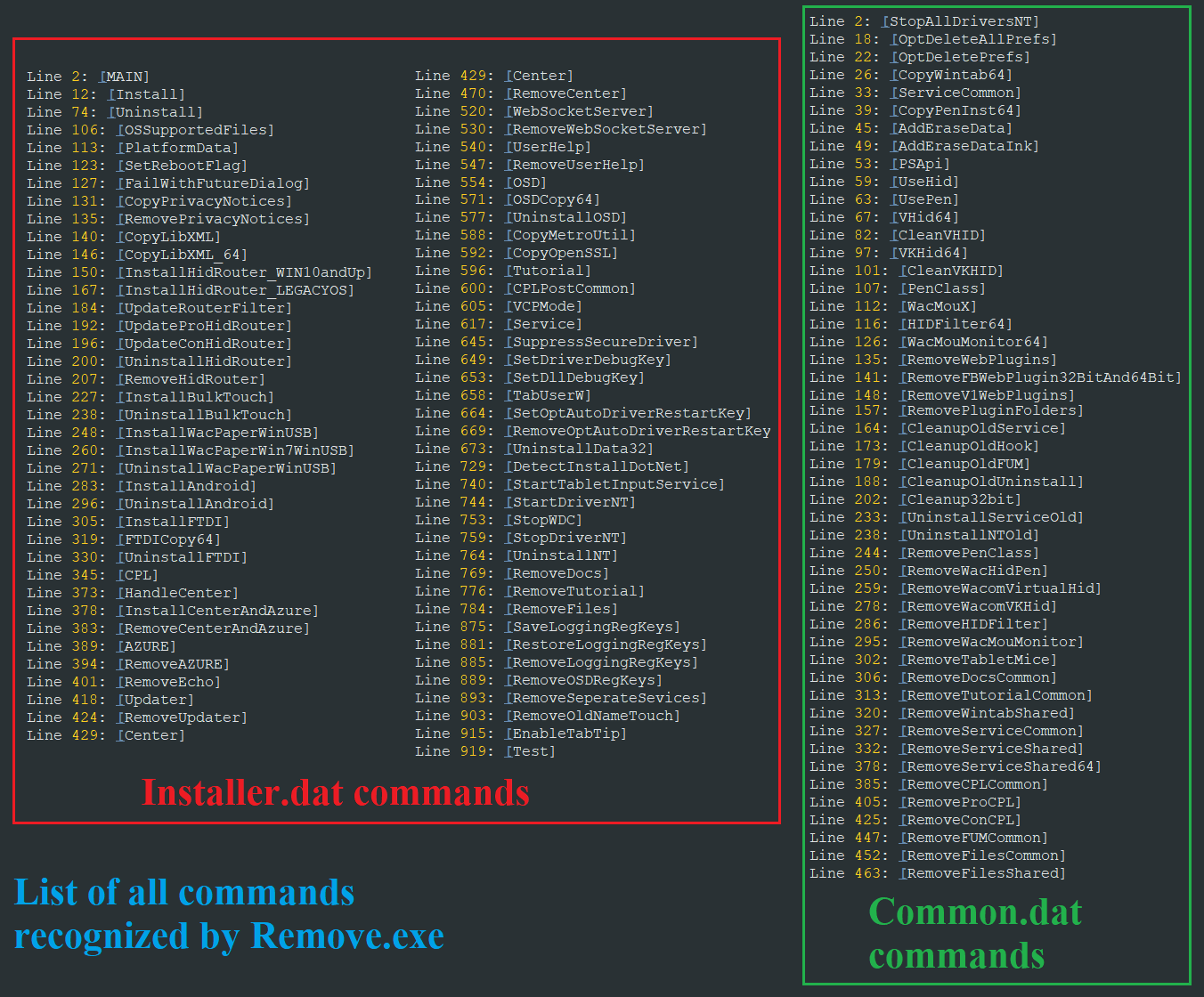
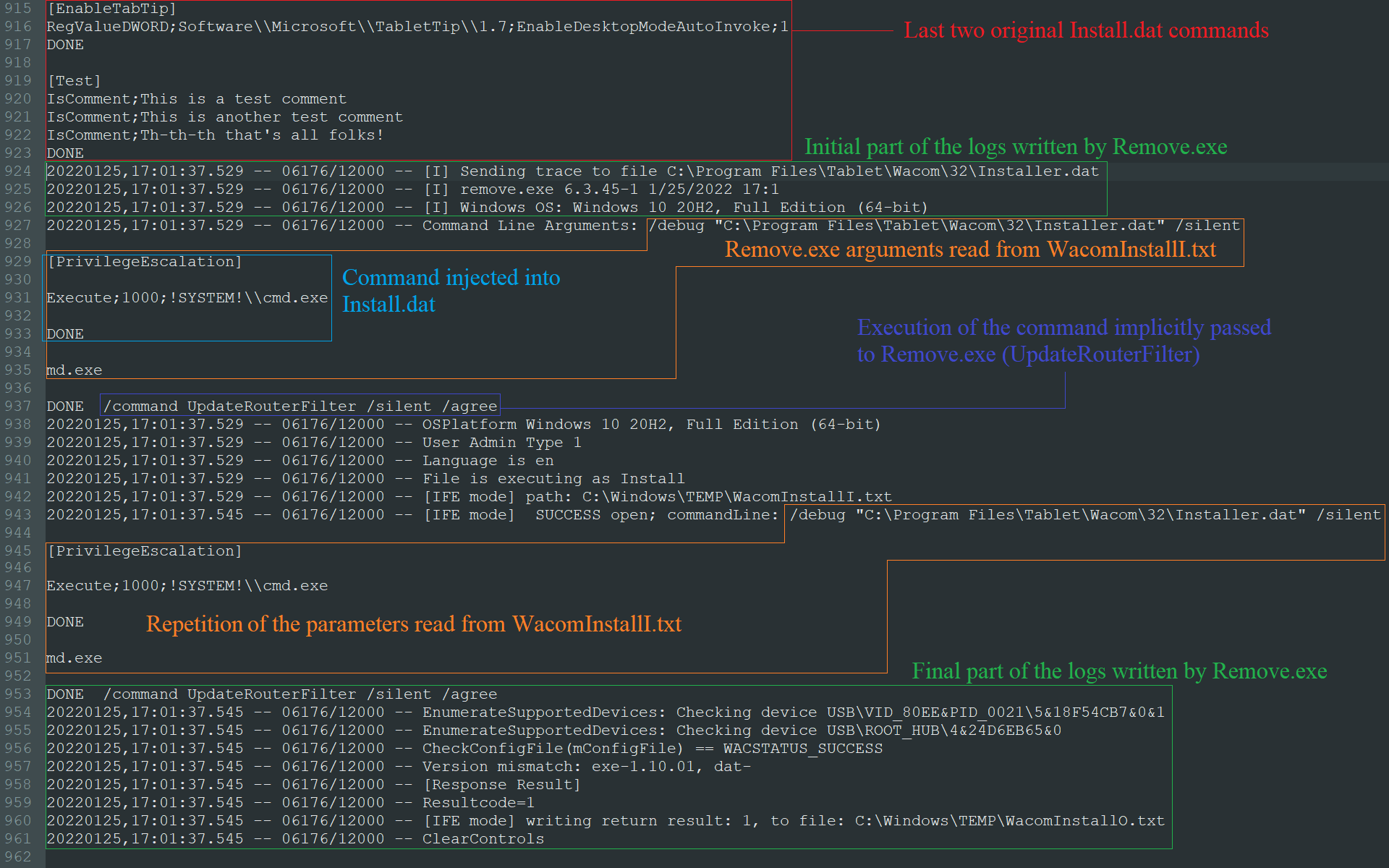
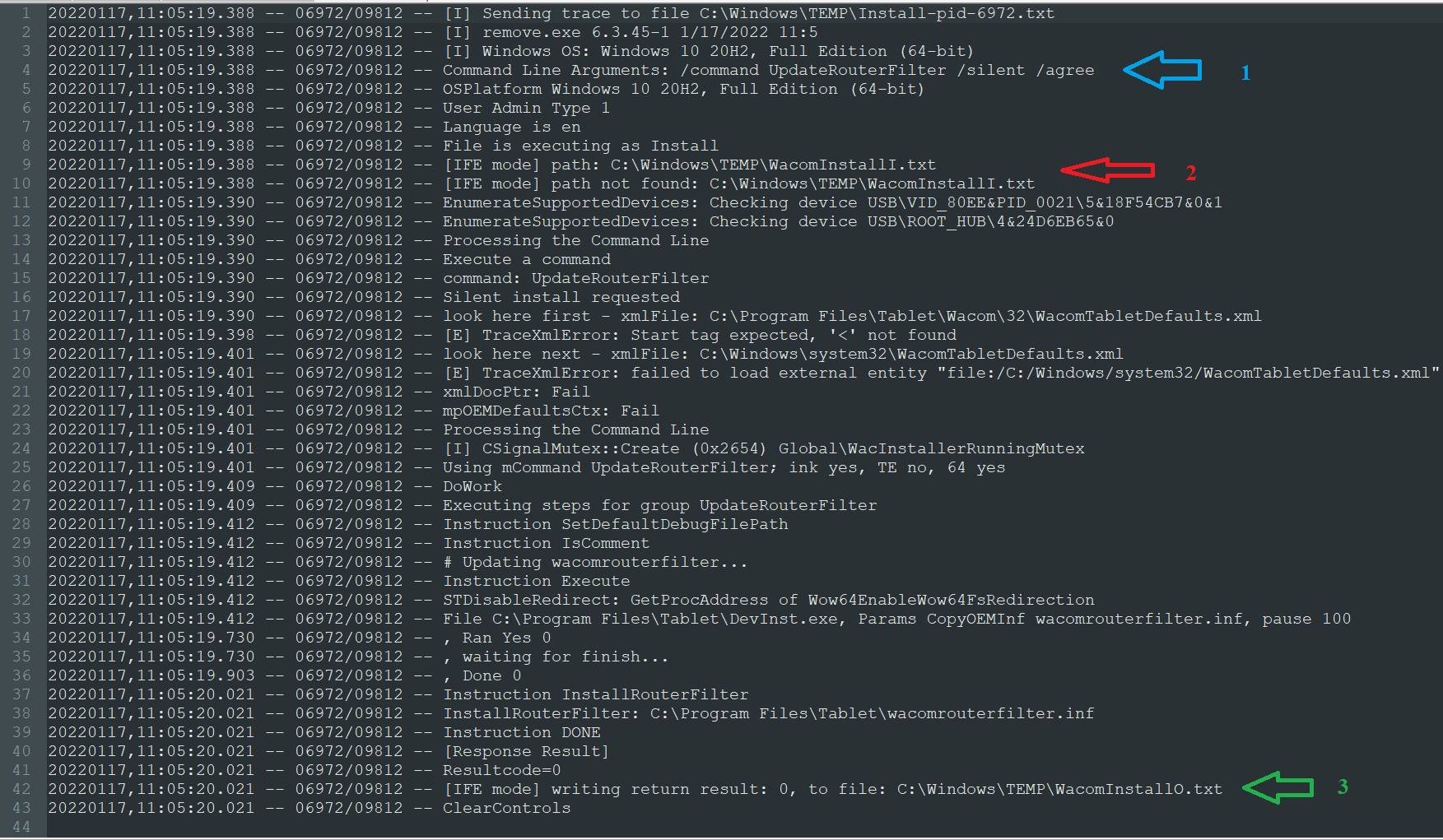
| /command commandName | Executes the commandName command. |
| /custom "fileName" | Copies C:\Program Files\Tablet\Wacom\32\CustomDefaults\fileName.xml to C:\Program Files\Tablet\Wacom\WacomTabletDefaults.xml |
| /debug "C:\foo.txt" | Writes the logs generated during the execution of a command into C:\foo.txt file. |
| /d "C:\foo.txt" | Writes the logs generated during the execution of a command into C:\foo.txt file. |
| /from-ife | ??? Can it be related to the graphics tablet Integrated Front End ??? |
| /hex "C:\...\foo.txt" | Converts C:\...\foo.txt to hexadecimal format and saves the converted file to C:\...\foo.txt.txt |
| /ink | Request Ink installation. |
| /opt nowdc | nohelp | noinet | DebugDrv | DebugDll | Read this page for the description of the different options. |
| /silent | Avoids the license agreement window (and any other windows) pop-up. |
| /s | Avoids the license agreement window (and any other windows) pop-up. |
| /uninstall | Uninstalls Wacom Driver. |
| /u | Uninstalls Wacom Driver. |